MOOVE Platform consists of Mobile Applications for Driver and Employees and Web Applications for Operators and Employers. MOOVE’s multitiered architecture can be separated into three tiers: UX Clients (applications) for experience delivery, Web Services for Application and Services Delivery. The Data layer is abstracted as a Service.
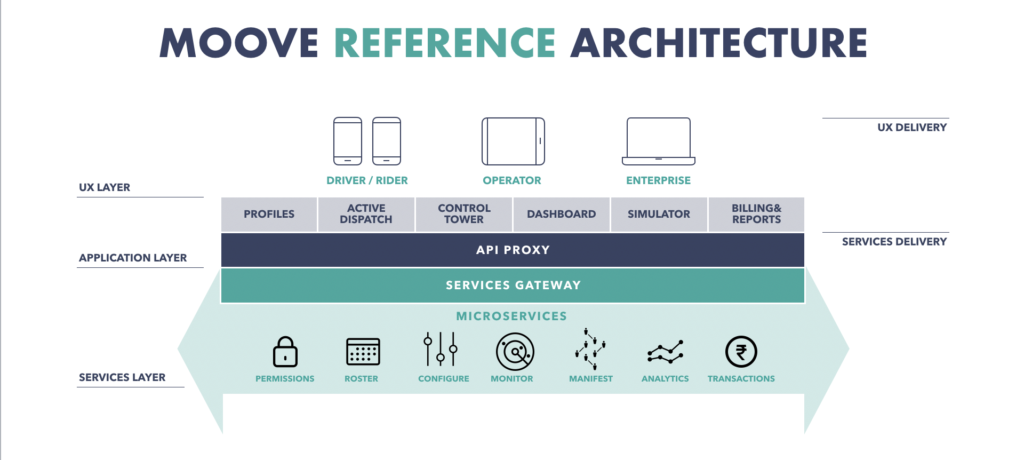
From a concrete Architecture perspective, MOOVE was realized using the Ruby on Rails framework, to create database-backed web applications using the Model-View-Controller (MVC) pattern.

MVC divides an application into three layers, each with a specific responsibility.
The Model layer represents your domain model (such as Account, Product, Person, Post, etc.) and encapsulates the business logic that is specific to your application.
The View layer is composed of “templates” that are responsible for providing appropriate representations of an application’s resources. Views are typically rendered to generate a controller response or to generate the body of an email.
The Controller layer is responsible for handling incoming HTTP requests and providing a suitable response. Usually this means returning HTML, but Rails controllers can also generate XML, JSON, PDFs, mobile-specific views, and more.
MOOVE Clients access the ROR backend via APIs exposed via ROR. Applications (Tier III) communicate with the Server (Tier II) using the REST API. REST API is the mechanism which is built on top of HTTP protocol and allows easy flow of information across internet, taking data security into account. The REST APIs are exposed by the Server for the applications to access data out of the data store (Tier I).
Thus the applications do not have direct access to the data store and all requests to the database are routed through the server. This is a step towards securing the data store from any kind of attacks from the applications as it ensures that all times, only the server has a direct connection with the Data Store. Further, requests from authenticated applications only are accepted by the server.
Members: please use the Link(s) below to download the document(s).
Don’t see the Link(s) above? Please Sign-in / Register as a Member.